Blogs
Read our latest blog for insightful tips and knowledge!
Filter by

Enhancing Cloud Security Like No Other with BrainIAC
In the dynamic landscape of cloud computing, security remains a paramount concern. As organizations increasingly…
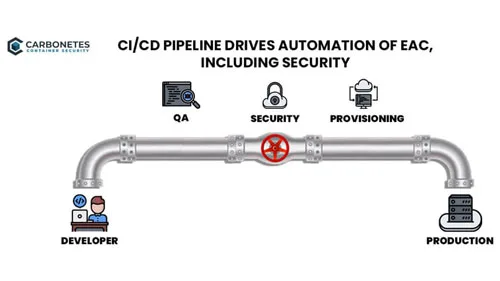
Security & CI/CD Toolchains
Modern security tools provide a variety of implementation options including full-function clients, APIs and CI/CD…
5 Container Security Trends to Watch Out For in the Near Future
In the next few years, we will see a continued increase in the use of…

Continuous Monitoring in Container Security: Safeguarding Your Digital Ecosystem
Security is paramount in the containerized applications landscape, where agility meets complexity. Traditional security measures…
5 Things AI Code Writing Can't Do in DevOps: Why Human Developers Remain Essential
Artificial intelligence (AI) has become an increasingly popular tool for automating repetitive tasks and increasing…

Why Container Security Experts Are Necessary
As the world moves more of its infrastructure and applications to container platforms like Docker,…

4 Advantages of Cloud-Native Container Security
Cloud-native container security is a security model that focuses on protecting containers and the microservices…

Docker Registry: An Essential Tool for Container Image Management
Docker Registry is a critical component in the Docker ecosystem. It serves as a central…

Why Should You Leave Container Security in The Hands of Experts
Container security is a critical part of any organization's infrastructure and must be handled with…

The Advantages of Cloud-Native Security in Building Secure Applications
From computing down to data storage, cloud-native security is quickly becoming the preferred choice for…
