Blogs
Read our latest blog for insightful tips and knowledge!
Filter by

The Best Ways to Increase DevOps Productivity
As technology progresses, businesses realize the importance of increasing their DevOps productivity. With the development…

How Your Business’s App Can Benefit From Having Container Security Management
As the world increasingly moves towards a digital landscape, more and more businesses are turning…

Embracing Zero Trust: A Paradigm Shift in Container Security for Web Applications
Security remains a paramount concern. Traditional security models are often insufficient to combat the sophisticated…

The Key Benefits of Kubernetes in Container Management
Containerization has become an increasingly popular solution for organizations looking to deploy applications quickly and…

The Challenges in Container Security That Can Be Overlooked
Container security is becoming increasingly important in the world of cloud computing. As containers become…
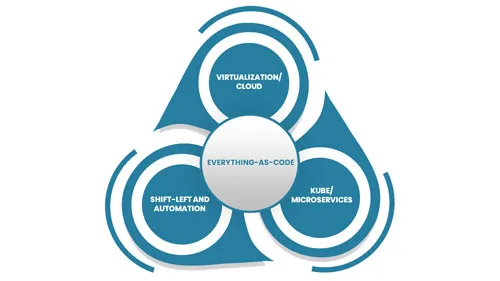
Everything-as-Code
Everything-as-Code (EaC) is the future of IT; the benefits are simply overwhelming. EaC is the…

The Intricacies of GenAI-Generated Code: Navigating the Challenges of Weak Links
Boosted by GenAI in the world of technology, code development has been vastly improved with…

Is Artificial Intelligence a Threat to Cybersecurity?
With the growth of technology, AI and cybersecurity have engendered questions about threats that may…

What's Next for IaC and Cloud-Native Container Security in 2024?
The cloud-native revolution has transformed how we develop and deploy applications. Infrastructure as code (IaC)…

Why You Need Humans in Securing AI-Generated Code
Artificial intelligence (AI) is revolutionizing our world, and software development is no exception. AI-powered coding…
