Blogs
Read our latest blog for insightful tips and knowledge!
Filter by

The Most Common Container Security Mistakes That You Must Avoid This 2023
New attacks might be lurking in the new year, but security professionals and IT leaders…

Continuous Monitoring in Container Security: Safeguarding Your Digital Ecosystem
Security is paramount in the containerized applications landscape, where agility meets complexity. Traditional security measures…

Why BOM Diggity is the Superior Container Security Platform
In an era where software security is a top concern, organizations must prioritize measures to…

The Challenges in Container Security That Can Be Overlooked
Container security is becoming increasingly important in the world of cloud computing. As containers become…
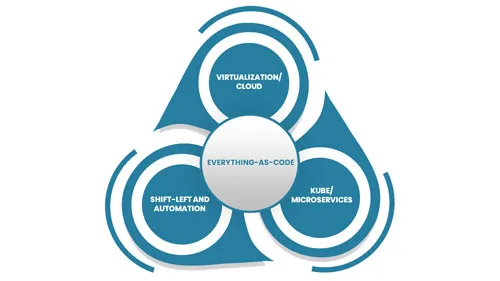
Everything-as-Code
Everything-as-Code (EaC) is the future of IT; the benefits are simply overwhelming. EaC is the…

Enhancing Container Security with Carbonetes - Lite App: A Comprehensive Overview
Container security plays a crucial role in safeguarding sensitive data and preventing potential vulnerabilities in…

Continuous Monitoring in Container Security: Safeguarding Your Digital Ecosystem
Security is paramount in the containerized applications landscape, where agility meets complexity. Traditional security measures…

Embracing Zero Trust: A Paradigm Shift in Container Security for Web Applications
Security remains a paramount concern. Traditional security models are often insufficient to combat the sophisticated…

The Importance of SBOMs in Managing IoT Software Security
Building with open-source software is essential for many IoT developers. Open-source software provides a wealth…

Using IaC to Manage Edge Computing Infrastructure
Edge computing is the distribution of computing power and data storage closer to where data…
