Blogs
Read our latest blog for insightful tips and knowledge!
Filter by

Containerized Deployment Strategies for DevOps Teams
Containerization is changing the way that DevOps teams approach application deployment. By providing a portable,…

What's Next for IaC and Cloud-Native Container Security in 2024?
The cloud-native revolution has transformed how we develop and deploy applications. Infrastructure as code (IaC)…

How Container Security Refines DevOps Practices
In the ever-evolving software development landscape, the symbiotic relationship between DevOps and containerization has revolutionized…
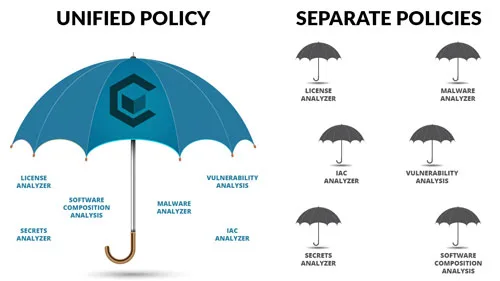
Choosing the Right Security Policy Solution
Security policies are a critical component of your security solution and selecting the right security…

4 Advantages of Cloud-Native Container Security
Cloud-native container security is a security model that focuses on protecting containers and the microservices…
Creating Effective Docker Images with the Help of Container Security
There are times Docker images are created without much thought to security. However, given the…

The Challenges in Container Security That Can Be Overlooked
Container security is becoming increasingly important in the world of cloud computing. As containers become…
The Benefits of Network Functions Visualization
Software development teams, network operators and service providers all benefit from using Network Functions Visualization…
The Importance of Dependency Injection
Developers of the modern tech landscape are familiar with the concept of dependency injection and…

The Advantages of Containers Over Virtual Machines
Virtual machines changed the way IT departments delivered services, significantly increasing the speed and efficiency…
